Partner not found
Poetry
The AI workspace for experienced hire talent acquisition.

Overview
Poetry is the AI workspace for talent acquisition, allowing you to manage and develop all the assets you need to work on every req, including talent intelligence, talent sourcing assets, recruitment marketing content and operational recruiting materials.
Integration details
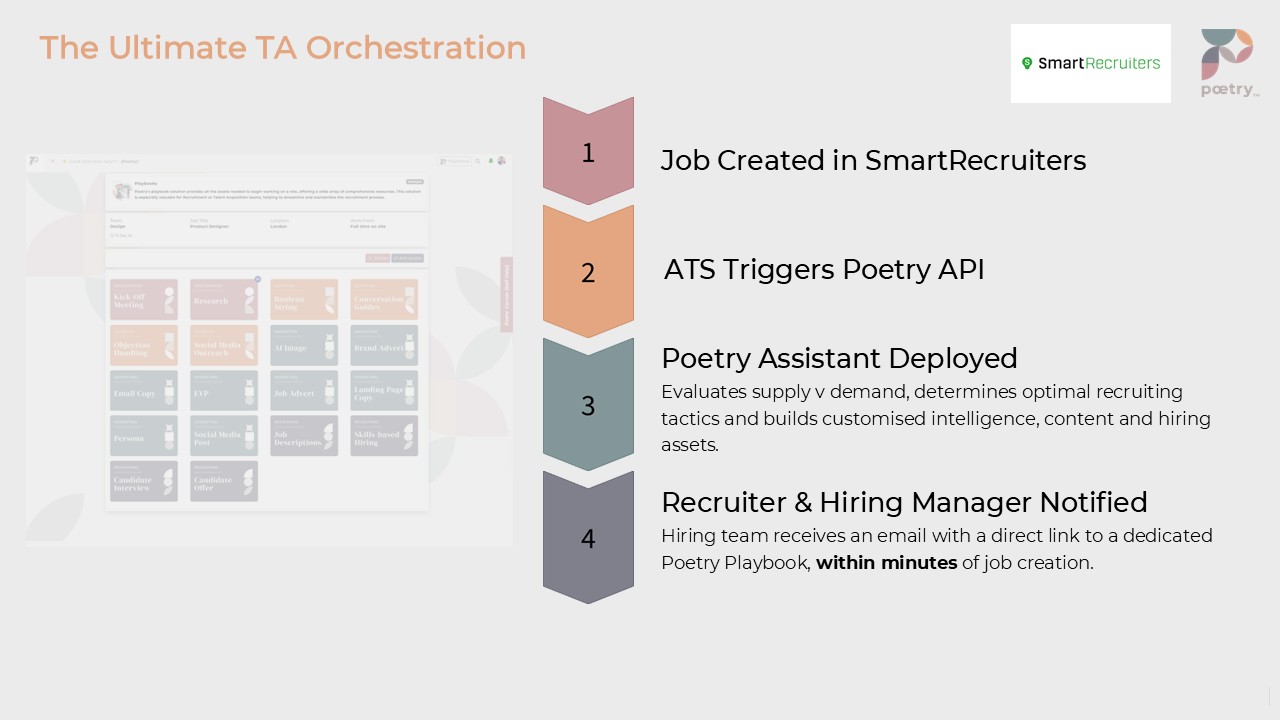
Enable the integration and when you log your req in SmartRecruiters, Poetry receives a signal, gets to work, builds a 'Playbook' of assets which are on-brand, in-context, right-first-time and in your email inbox within 2 minutes. The Playbook includes all the talent intelligence, talent sourcing assets, recruitment marketing content and operational recruiting materials for you to wow hiring managers, inspire candidates and achieve enhanced success.
Media
Features
The Talent Acquisition Playbook for Every Req
Poetry's Playbook solution develops a pack of assets for every req within 20 seconds, saving recruiters vast amounts of time and enabling them to be more productive and successful. The Playbook includes 17 essential items of talent intelligence, talent sourcing assets such as Boolean strings and outreach messaging, recruitment marketing content including job adverts and social media posts and operational recruiting materials including the job description and interview questions.
Admin settings and configuration options ensure every Playbook is on-brand, in-context and right first time. Check out an example here:
https://youtu.be/nYu0VnHXDLs
Admin settings and configuration options ensure every Playbook is on-brand, in-context and right first time. Check out an example here:
https://youtu.be/nYu0VnHXDLs
Resources
FAQ
Legal company name | Poetry HR Ltd |
Outline of service | Provision of software as a service for HR teams |
Cloud service | SaaS |
Description of systems | Azure-hosted system consisting of Angular front-end components, Python Django back-end with Postgres database. |
Physical locations where data stored | Azure-hosted UK South |
How would the data stored and/or processed by this system be classified? | Private and confidential |
Do you provide consultative services? | No |
Do you have independent third party certifications? | We are ISO27001 certified and in the process of securing SOC2. |
Does your company have a security policy? | Yes | PoetryHR Security Policy.pdf
Is your security policy signed off by a senior executive? | Yes, director and co-founder Mike Hughes |
Is your security policy based on a standardised framework? | Yes, ISO27001 |
Are your security policies reviewed at least annually? | Yes |
Does your company have a security awareness programme? | Yes |
Does your company have a designated Information Security team? | Yes |
Are staff subject to pre-employment background checks? | Yes |
Do all staff members sign a confidentiality agreement? | Yes |
Does your company have a documented process for responding to security incidents? | Yes |
Does this process ensure that security incidents are reported through appropriate channels to customers? | Yes |
Will you report a confirmed data breach to customers in 72 hours or less? | Yes |
Does the data stored or processed by the system contain any financial information? | No |
Do your employees rendering services to customers have an adequate level of professional training? | Yes |
Does your solution provide for role based access controls (RBAC)? | Yes |
Does your solution integrate with SSO or SAML? | Yes |
Does your company have an information classification scheme? | No |
Are staff prohibited from using USB devices to remove data from your organization? | Yes |
Are all laptops and removable media encrypted? | No |
Does your company have a method for deleting customers' data at their request? | Yes |
Does your company provide encryption for data in-transit? | Yes | TLS protocol, SSL certificates, Azure security features and PostgreSQL configuration
Does your company provide encryption for data at-rest? | Yes | 256-bit AES encryption
Does your solution use or require agents? | No |
Do all laptops have antivirus installed to protect against malware? | Yes |
Do you have the capability to perform a remote-wipe on devices if lost or stolen? | No |
Will you be storing any customer data locally to workstations or laptops? | No |
Do all staff use their own system ID and password which is not shared? | Yes |
Will access to customers' information be limited to specific staff within specific locations? | Yes |
Are system access privileges reviewed at least annually? | Yes |
Are privileged accounts reviewed at least quarterly? | Yes |
Are logs of all system activity retained for a specified length of time? | Yes | 7 days
Do you immediately revoke and/or disable system all access for terminated staff? | Yes | On day of termination
Is remote access to your networks permitted? | Yes | Via secured whitelist of IP addresses
Are passwords configured to be changed at least annually? | Yes |
Is appropriate segregation of duties in place? | Yes |
Are your staff based in offices with an access card system? | No | Staff work remotely
Are access cards revoked and deactivated immediately upon staff termination? | No | Staff work remotely
Are all visitors issued cards retrieved and terminated on departure? | No | We have no physical premises
Do access logs record everyone (including visitors) who entered the facility and when ? | No | We have no physical premises
Are the premises subject to 24/7 CCTV monitoring? | No | We have no physical premises
Do you retain access logs and CCTV recordings for at least 180 days? | No | We have no physical premises
Does your company have guards or cleaners with unescorted access to the interior of the premises? | No | We have no physical premises
Are your servers located in the US and/or EU? | No | United Kingdom
Are your servers in secured rooms with an access card system? | Yes | Azure UK South
Is access to server rooms restricted to authorized personnel only? | Yes |
Is your corporate infrastructure leveraged as part of the service offering to customers? | Yes |
Are all system changes managed through a Change Approval/Control process? | Yes |
Are the development and test environments distinct and separated from the production environment? | Yes |
Do all employee laptops and desktops feature firewalls? | Yes |
Does your company perform regular backups of critical systems? | Yes |
Are server/firewall logs retained for a specific period of time? | Yes | 90 days
Are patch management processes in place? | Yes | via Azure App Services
Are servers regularly scanned for vulnerabilities? | Yes |
Is a minimum baseline configuration of information technology systems established and maintained to incorporate security principles? | Yes |
Are all assets (hardware, software, information, etc.) clearly identified and maintained in a current asset inventory? | Yes |
Is there a software inventory in place to manage and track software licenses? | Yes |
Do you employ an industry standard System Development Life Cycle (SDLC) methodology? | No |
Do you utilize secure coding standards? | No |
Do you perform Dynamic Application Security Testing (DAST) of your product(s)? If so, explain. | Yes | OWASP ZAP
Do you perform Static Application Security Testing (SAST) of your product(s)? If so, explain. | No |
Do you perform Software Composition Analysis (SCA) testing of your product(s) for 3rd party library and licensing issues? If so, explain. | No |
Do you have the ability to produce a Software Bill of Materials (SBOM) for your product(s) and would you be willing to provide it for further risk assessment? | Yes |
Does your company have a Business Continuity Management Program? | Yes | Business Continuity Management Plan.pdf
Do you conduct Business Continuity testing? | Yes |
How often is Business Continuity testing performed? | Annually |
Have you determined the expected recovery timeframe for the application/service that you would provide to Tenable following an incident? | Yes |
Please provide details, including timeframe | 1 day |
Have you determined the maximum data loss in the event of an incident? | No |
Will the service require you to have access to Tenable Employee's Personal Data? | No |
Will services be subcontracted, or otherwise involve the use of, additional third parties? | No |
Does your company maintain a list of all your service suppliers? | Yes |
Does your company maintain a list of service suppliers who are custodians of your data or have access to production system data? | Yes |
Does your company undertake security reviews of all such service suppliers? | Yes |
Does your company have a process to check where (e.g. in which country) your service suppliers will hold your data? | Yes |
Does your company have contractual clauses to ensure your service suppliers protect your data? | Yes |
Does your company's contractual clauses state that your service suppliers must assure the security of their service suppliers, so that all data custodians in the supply chain protect data appropriately? | Yes |
Is your company GDPR compliant? | Yes |
Do you comply with other data privacy frameworks? | No |
Please provide a detailed explanation of any integrations with other products. | All products are integrated using OAuth2 mechanisms. |
Does your product have an on-premise component where we will be able to install endpoint agents and manage the operating system? | No |
What protocols does your solution use for communication? | TLS version 1.2, full restful API on top of HTTPS |
Does your solution encrypt all protocols? | Yes |
What algorithms and ciphers are used by the protocols utilized by your solution? | SHA-256 (Secure Hash Algorithm 256-bit) |
Does your product support SSO? | Yes |
What data types are stored and/or processed by your product? | Marketing content, learning content, database content in all content formats |
How is our data protected? Do you support encryption at rest? | Yes |
Can your employees access our data? | Yes |
Does your product allow the viewing of our users' authentication logs? | No |
Do you have any security best practices that you recommend for your product? | Yes | Security Best Practices (2).pdf
Are independent third-party penetration tests conducted regularly for your product? | Yes |
Do you allow customers to perform assessment scans of your product? | Yes |
Are there any special access requirements for your product that may require access control changes in our environment? | No |
Does your product have support for redundancy/high availability? | Yes |
Please provide details on redundancy/high availability. | 99.999% availability |
Does your product use a SaaS-based model? | Yes |
Is customer data hosted in a multi-tenant environment? | Yes |
Please provide details, including information on physical and logical segregation controls. | Based on a unique workspace ID, database records are separated and file content is stored in a directory also based on unique workspace ID |
Does your company have a privacy compliance program to address compliance with privacy regulations (e.g., GDPR, CCPA/CPRA, PIPEDA, LGPD, APPI)? | No |
Does the service your Company provides require the processing of Personal Data provided by customers? | No |
Do you use artificial intelligence, machine learning, profiling, or automated decision-making technologies (collectively, "AI Tools") in, or to provide, your product/service? | Yes |
Describe the function of the AI Tools, including when/how the AI Tools may be used in connection with your product/service. | Integration with OpenAI and Perplexity for provision of content-generation assistance |
What data types may be processed to develop, operate, or improve the AI Tools? | Recruitment and recruitment marketing-related text and notes; no PII |
Which third party provides the AI Tools, if any? | OpenAI and Perplexity |
Have you taken steps to address risks regarding accuracy/reliability, bias/discriminatory impact, privacy, confidentiality, and transparency in connection with the AI Tools or their outputs (collectively, "AI Risks")? | Yes |
Do you use any third-party training, validation, and testing when developing, operating, or improving the AI Tools? | Yes |
Please provide details: | Expert training and consultancy from PPLBots and and Bellrock Technology |
Please describe any detected or suspected AI Risks and any related corrective/mitigating actions: | None |
Do you have a formal governance program to oversee AI Tools and manage AI Risks in your product/service? | No |
Have you taken any steps to align your program with any framework or code of conduct related to artificial intelligence, machine learning, or automated decision-making technologies? | No |
Have you taken steps to document the basis and logical reasoning for your AI Tools' outputs and any assumptions relied upon? | No |
Have you taken steps to monitor, assess, and correct/mitigate actual or suspected AI Risks? | Work with Bellrock Technology |
Outline of service | Provision of software as a service for HR teams |
Cloud service | SaaS |
Description of systems | Azure-hosted system consisting of Angular front-end components, Python Django back-end with Postgres database. |
Physical locations where data stored | Azure-hosted UK South |
How would the data stored and/or processed by this system be classified? | Private and confidential |
Do you provide consultative services? | No |
Do you have independent third party certifications? | We are ISO27001 certified and in the process of securing SOC2. |
Does your company have a security policy? | Yes | PoetryHR Security Policy.pdf
Is your security policy signed off by a senior executive? | Yes, director and co-founder Mike Hughes |
Is your security policy based on a standardised framework? | Yes, ISO27001 |
Are your security policies reviewed at least annually? | Yes |
Does your company have a security awareness programme? | Yes |
Does your company have a designated Information Security team? | Yes |
Are staff subject to pre-employment background checks? | Yes |
Do all staff members sign a confidentiality agreement? | Yes |
Does your company have a documented process for responding to security incidents? | Yes |
Does this process ensure that security incidents are reported through appropriate channels to customers? | Yes |
Will you report a confirmed data breach to customers in 72 hours or less? | Yes |
Does the data stored or processed by the system contain any financial information? | No |
Do your employees rendering services to customers have an adequate level of professional training? | Yes |
Does your solution provide for role based access controls (RBAC)? | Yes |
Does your solution integrate with SSO or SAML? | Yes |
Does your company have an information classification scheme? | No |
Are staff prohibited from using USB devices to remove data from your organization? | Yes |
Are all laptops and removable media encrypted? | No |
Does your company have a method for deleting customers' data at their request? | Yes |
Does your company provide encryption for data in-transit? | Yes | TLS protocol, SSL certificates, Azure security features and PostgreSQL configuration
Does your company provide encryption for data at-rest? | Yes | 256-bit AES encryption
Does your solution use or require agents? | No |
Do all laptops have antivirus installed to protect against malware? | Yes |
Do you have the capability to perform a remote-wipe on devices if lost or stolen? | No |
Will you be storing any customer data locally to workstations or laptops? | No |
Do all staff use their own system ID and password which is not shared? | Yes |
Will access to customers' information be limited to specific staff within specific locations? | Yes |
Are system access privileges reviewed at least annually? | Yes |
Are privileged accounts reviewed at least quarterly? | Yes |
Are logs of all system activity retained for a specified length of time? | Yes | 7 days
Do you immediately revoke and/or disable system all access for terminated staff? | Yes | On day of termination
Is remote access to your networks permitted? | Yes | Via secured whitelist of IP addresses
Are passwords configured to be changed at least annually? | Yes |
Is appropriate segregation of duties in place? | Yes |
Are your staff based in offices with an access card system? | No | Staff work remotely
Are access cards revoked and deactivated immediately upon staff termination? | No | Staff work remotely
Are all visitors issued cards retrieved and terminated on departure? | No | We have no physical premises
Do access logs record everyone (including visitors) who entered the facility and when ? | No | We have no physical premises
Are the premises subject to 24/7 CCTV monitoring? | No | We have no physical premises
Do you retain access logs and CCTV recordings for at least 180 days? | No | We have no physical premises
Does your company have guards or cleaners with unescorted access to the interior of the premises? | No | We have no physical premises
Are your servers located in the US and/or EU? | No | United Kingdom
Are your servers in secured rooms with an access card system? | Yes | Azure UK South
Is access to server rooms restricted to authorized personnel only? | Yes |
Is your corporate infrastructure leveraged as part of the service offering to customers? | Yes |
Are all system changes managed through a Change Approval/Control process? | Yes |
Are the development and test environments distinct and separated from the production environment? | Yes |
Do all employee laptops and desktops feature firewalls? | Yes |
Does your company perform regular backups of critical systems? | Yes |
Are server/firewall logs retained for a specific period of time? | Yes | 90 days
Are patch management processes in place? | Yes | via Azure App Services
Are servers regularly scanned for vulnerabilities? | Yes |
Is a minimum baseline configuration of information technology systems established and maintained to incorporate security principles? | Yes |
Are all assets (hardware, software, information, etc.) clearly identified and maintained in a current asset inventory? | Yes |
Is there a software inventory in place to manage and track software licenses? | Yes |
Do you employ an industry standard System Development Life Cycle (SDLC) methodology? | No |
Do you utilize secure coding standards? | No |
Do you perform Dynamic Application Security Testing (DAST) of your product(s)? If so, explain. | Yes | OWASP ZAP
Do you perform Static Application Security Testing (SAST) of your product(s)? If so, explain. | No |
Do you perform Software Composition Analysis (SCA) testing of your product(s) for 3rd party library and licensing issues? If so, explain. | No |
Do you have the ability to produce a Software Bill of Materials (SBOM) for your product(s) and would you be willing to provide it for further risk assessment? | Yes |
Does your company have a Business Continuity Management Program? | Yes | Business Continuity Management Plan.pdf
Do you conduct Business Continuity testing? | Yes |
How often is Business Continuity testing performed? | Annually |
Have you determined the expected recovery timeframe for the application/service that you would provide to Tenable following an incident? | Yes |
Please provide details, including timeframe | 1 day |
Have you determined the maximum data loss in the event of an incident? | No |
Will the service require you to have access to Tenable Employee's Personal Data? | No |
Will services be subcontracted, or otherwise involve the use of, additional third parties? | No |
Does your company maintain a list of all your service suppliers? | Yes |
Does your company maintain a list of service suppliers who are custodians of your data or have access to production system data? | Yes |
Does your company undertake security reviews of all such service suppliers? | Yes |
Does your company have a process to check where (e.g. in which country) your service suppliers will hold your data? | Yes |
Does your company have contractual clauses to ensure your service suppliers protect your data? | Yes |
Does your company's contractual clauses state that your service suppliers must assure the security of their service suppliers, so that all data custodians in the supply chain protect data appropriately? | Yes |
Is your company GDPR compliant? | Yes |
Do you comply with other data privacy frameworks? | No |
Please provide a detailed explanation of any integrations with other products. | All products are integrated using OAuth2 mechanisms. |
Does your product have an on-premise component where we will be able to install endpoint agents and manage the operating system? | No |
What protocols does your solution use for communication? | TLS version 1.2, full restful API on top of HTTPS |
Does your solution encrypt all protocols? | Yes |
What algorithms and ciphers are used by the protocols utilized by your solution? | SHA-256 (Secure Hash Algorithm 256-bit) |
Does your product support SSO? | Yes |
What data types are stored and/or processed by your product? | Marketing content, learning content, database content in all content formats |
How is our data protected? Do you support encryption at rest? | Yes |
Can your employees access our data? | Yes |
Does your product allow the viewing of our users' authentication logs? | No |
Do you have any security best practices that you recommend for your product? | Yes | Security Best Practices (2).pdf
Are independent third-party penetration tests conducted regularly for your product? | Yes |
Do you allow customers to perform assessment scans of your product? | Yes |
Are there any special access requirements for your product that may require access control changes in our environment? | No |
Does your product have support for redundancy/high availability? | Yes |
Please provide details on redundancy/high availability. | 99.999% availability |
Does your product use a SaaS-based model? | Yes |
Is customer data hosted in a multi-tenant environment? | Yes |
Please provide details, including information on physical and logical segregation controls. | Based on a unique workspace ID, database records are separated and file content is stored in a directory also based on unique workspace ID |
Does your company have a privacy compliance program to address compliance with privacy regulations (e.g., GDPR, CCPA/CPRA, PIPEDA, LGPD, APPI)? | No |
Does the service your Company provides require the processing of Personal Data provided by customers? | No |
Do you use artificial intelligence, machine learning, profiling, or automated decision-making technologies (collectively, "AI Tools") in, or to provide, your product/service? | Yes |
Describe the function of the AI Tools, including when/how the AI Tools may be used in connection with your product/service. | Integration with OpenAI and Perplexity for provision of content-generation assistance |
What data types may be processed to develop, operate, or improve the AI Tools? | Recruitment and recruitment marketing-related text and notes; no PII |
Which third party provides the AI Tools, if any? | OpenAI and Perplexity |
Have you taken steps to address risks regarding accuracy/reliability, bias/discriminatory impact, privacy, confidentiality, and transparency in connection with the AI Tools or their outputs (collectively, "AI Risks")? | Yes |
Do you use any third-party training, validation, and testing when developing, operating, or improving the AI Tools? | Yes |
Please provide details: | Expert training and consultancy from PPLBots and and Bellrock Technology |
Please describe any detected or suspected AI Risks and any related corrective/mitigating actions: | None |
Do you have a formal governance program to oversee AI Tools and manage AI Risks in your product/service? | No |
Have you taken any steps to align your program with any framework or code of conduct related to artificial intelligence, machine learning, or automated decision-making technologies? | No |
Have you taken steps to document the basis and logical reasoning for your AI Tools' outputs and any assumptions relied upon? | No |
Have you taken steps to monitor, assess, and correct/mitigate actual or suspected AI Risks? | Work with Bellrock Technology |
£100 / $135 per user per month / 2-year contract.